Lupine Publishers Group
Lupine Publishers
Menu
ISSN: 2643-6744
Mini Review(ISSN: 2643-6744) 
Mini Overview of Key Issues in Routing for OSPF MANETs Volume 1 - Issue 2
Alamgir Naushad*, Muhammad Tanveer and Abd Ullah Khan
- Faculty of Computer Sciences and Engineering, GIK Institute of Engineering Sciences and Technology, Pakistan
Received:January 28, 2019; Published:February 04, 2019
*Corresponding author: Alamgir Naushad, Faculty of Computer Sciences and Engineering, GIK Institute of Engineering Sciences and Technology, Topi 23640, Pakistan
DOI: 10.32474/CTCSA.2019.01.000109
Abstract
Open Shortest Path First (OSPF) is a well known and prominent Internet Protocol (IP) for network routing. By deploying a link state routing (LSR) algorithm OSPF comes under the category of interior gateway routing protocols. In today’s wireless ad hoc Internet, the current routing domain needs to maintain a peak level of service accessibility and availability, thus OSPF must be extended to the wireless ad hoc network for maximizing routing performance in the network by taking into account key routing issues, i.e., optimal Hello Interval, efficient flooding schemes, optimizing the traffic engineering related issues, optimum adjacency creations, connectivity factors, reducing control overhead, and QoS and security challenges. In addition, OSPF is very effective in its adoption of handling the network bandwidth utilization, therefore, wireless capacity planning is of utmost importance for today’s Internet with the possible presence of wireless infrastructure. Improving routing stability in OSPF MANET under topology change(s) due to variation in link connectivity becomes a very demanding challenge for the research community. Given a fascinating volume of review for literature and unavoidable importance relating to OSPF extension to MANETs, there has still persist a need to highlight key issues related with routing in OSPF MANET.
Keywords: MANETs; Routing; OSPF; Traffic Engineering; Connectivity Factors; Capacity Planning; Flooding Schemes
Introduction
Open Shortest Path First (OSPF) is a very well-known and prominent interior gateway protocol (responsible for routing) in the today’s Internet [1]. The routing functionality of such protocols can be seen within the domain, which can be, but not necessarily, is part of or contained within an autonomous system (AS). OSPF as part of the routing protocol comes under the group of link state routing protocol, which generally allows every router present in the network to learn about the complete network topology [2]. However, in order to achieve maximum routing performance, it is now for almost more than 3 decades that the Internet protocols for link state routing has been deployed in the Internet on the regular basis. When we go back in history, the first major and functional link state routing protocol was deployed in the year 1978, called the Shortest Path First (SPF) by replacing the popular distance vector approach in ARPANET at that time.
The OSPF Protocol is now being used by the Internet Service Providers (ISPs) for almost more than 25 years as a link state routing functionality in providing the Internet infrastructure. The maximum years of experience running with the OSPF Protocol and its wide spread deployment has put a lot of confidence in using it as a reliable and stable link state routing and has demanded and motivated the researchers from all over the world to put in the efforts to create room for further improvements and enhancements in its application for extending its operation to wireless ad hoc media in MANETs. As a matter of fact, the quality of service (QoS) requirements and the attributes of the routing infrastructures in MANETs is a demanding challenge as the network topology is frequently changing due to mobility [3,4].
The objective function of the OSPF-MANET Protocol is to provide highly scalable routing functionality and more flexible and robust operation on complex and highly dense networks. The prime concern in today 0 s wireless media is to somehow keep in limit the bandwidth processing requirements of the protocol while recovering from the network failure (Speed of Convergence) in the network topology is the prime concern [3,5]. Whenever there is a triggered event in the OSPF-MANET domain, in such case the protocol may typically required a few tens of seconds for recovering from any sort of router/link failure (network failure). During this ephemeral state, the network quality of service availability would go through a serious degradation or deterioration or in other cases there may be a complete breakdown of the network.
With the establishment of real time operations for certain applications over the Internet, (e.g. online video con-ferencing) or networked voice over IP from almost a previous decade, network service deterioration/ disruption for applications with quick response time, a few tens of seconds (network recovery time) can no more be permitted or accepted. The need to quickly recover from the failure has motivated the research community to present the possible scenarios to improve the OSPF Speed of Convergence and also to provide other proactive approaches and strategies for protecting the network traffic in the interim process [6]. One of the critical and important requirements for the today0 s routing infrastructure has highlighted the need of maximizing routing performance in response to the topology change.
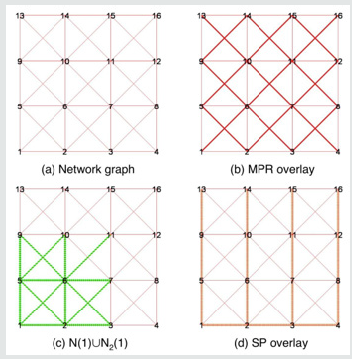
Significantly, reducing the bandwidth/processing requirement of the Internet routing protocol persuades to be the crucial framework as before. As the OSPF protocol being distributed in nature, it incorporates the within limit execution of the certain operations like processing and generation of the Hello packets by the active routers taking part in it [7]. It is important to mention here that the routers may not be highly overloaded, so that it may continuously decline to do/perform these critical network resource management operations. Such failures may contribute to the network failure and eventually result in the complete shutdown of the entire network. Hence, a novel scheme, refereed to as multi point relay (MPR) based MANET is introduced to tackle this issue, as presented in (Figure 1).
Conventionally, OSPF routing protocol has been employed as the network framework including a wired connectivity by exhibiting the largely static regional network topology. However, in the recent times routing infrastructure incor-porates the wireless components of the network too. These chunk subsist of either mobile or static network devices, possibly going out or coming in of each other’s mobile wireless range, or a hodgepodge of both. An illustration/ case of such kind of network can be classified as wireless, mobile ad hoc networks (MANETs) of objects where some objects exhibits mobile wireless connections with one or more conventional wired network(s) running under OSPF routing protocol. In a pragmatic scenario, lots of routing protocols have been devised to operate for the MANET, by using the selected routing protocol for MANET environment; the complex exchange process is required in such case while going through a transition step for the routing information of OSPF between this protocol and the other protocol that is targeted. In such situation, the exchange process might not evade/shun path for sub optimality. In such compelling situations, there is a high demand to enhance routing protocol in MANETs for OSPF domain by providing routing functionality and to intelligently assimilate the wireless and the wired peripherals of a network in the routing world.
This argument presented above incorporates a view of multiple proposals to enhance OSPF for its operation on MANETs. Researches for the last 2 decades have proposed multiple optimized OSPF routing protocols for MANET by suggesting the reduced number of re-transmissions, which are redundant in nature while disseminating a broadcast message throughout the entire network and, thus efficiently reducing the computational overhead of the active control traffic. This proposal eventually enhance the main characteristics of maximizing routing performance by highlighting the precise demands of the MANET networking. A few of those techniques out of the mentioned proposal present in the paper may be applied to the wireless network and has the capability to significantly improving both the Convergence speed and the Scalability factor of the OSPF networks having wireless connectivity.
Introduction to Routing in MANETs
Mobile ad hoc Networks (MANETs), which are also called Mesh Networks, are characterized by the way in which nodes are placed in such a manner that give pathways to data to be routed from the user to the desired destination. In the event that one of the intermediate node were to come up short (e.g. that user leaves the range), the system will naturally reconfigure itself, locating a substitute way from the user to the router [3,6]. Normally, all accessible nodes additionally arrange users, each sharing the aggregate data exchange limit (total capacity) of the operational hardware and operating protocol being incorporated. The network could likewise associate users to different routers straightforwardly, as would be done in a modern control and monitoring network. Since there is no requirement for central organization of the network setup, it is most proficient to outline the framework for independent operation of each node. In a modern domain, a circumstance, for example, an alert would be engendered through the network and reached directly by each node. Each node would be customized to react as per its specific requirement machine control, handle observing, supervisory work force or central office.
MANETs decide their arrangement periodically under topology change in the network. Every node identify the nodes that are accessible for communications, on the basis of signal strength, which is essentially identified with separation between nodes, but on the other hand is influenced by interference or obstructions [8]. A nodes may be remote, others might be perceptible yet have insufficient signal strength for reliable communications. Once the accessible nodes are distinguished, this information is communicated to different nodes, along network topology regarding the desired destination. Incorporating the network configuration algorithms, the system setup calculations to choose a specific route for every user to its destination. This procedure requires system operating software to have better decision making algorithms in light of pragmatic criteria for signal strength, reliability of path over time, and configuration parameters for network [9]. After some time, or even close persistently, the network will change. Users may go back and forth, nodes might be in motion, or changes in the electromagnetic environment may modify the spread between nodes. As these progressions occur, the network will overhaul its design and distinguish new paths from users to destinations [3,8]. This kind of reconfiguration will be rehashed again and again as the network changes. It is important to mention here that this is a similar procedure being incorporated on part of the Internet, where system loading and other hardware issues require redirection of user’s information through different routers [2].
The key advantages of ad hoc network includes autonomy from central administration of network, self-arranging, nodes behave as routers, self-healing through nonstop re-arrangement, scalabilitymake room for the expansion of more nodes and flexibility-like having the capability to get to the Internet from various different areas. While MANETs are normally utilized where they have the best accentuation on its advantages, there are a few confinements: Every node must have full execution, throughput is influenced by system loading, reliability requires an adequate number of accessible nodes. Finally, sparse networks can have routing issues [10].
Large networks can have inordinate latency (time delay), which influences a few applications. Some of these restric-tions additionally apply to traditional hub-and-spoke based networks (like OSPF) or can’t be tended to/by interchange setups. For instance, all networks are influenced by system loading, and networks with couple of nodes are hard to legitimize in hard-wired arrangements [5]. Wireless local area network (W-LAN) is the underlying application that got a deliberate advancement exertion. Shared networks of PC/PDA users have become familiar in this regard. Commercial wireless Internet service providers (WISP) incorporate repeater nodes to extend to large coverage area, while user nodes can extend service in their local area. Control systems (e.g. natural controls) and industrial monitoring of different processes and control are getting to be significant applications for mesh networking. These environments are hard to present with devoted wiring, being spread over a vast area, frequently with troublesome access.
Key Issues with OSPF MANETs
Some of the important issues regarding MANETs are security, routing, hidden terminal problem, bandwidth, power limitation and corroboration of mobile devices. Safeguarding the data communication in MANETs is one of the key aspect to be addressed. It is important to mention here that MANETs are highly dynamic in nature where topology changes, for instance the link breakage happens quite frequently [5,9]. Thus, we need a security mechanism which is dynamic in nature too. Some of the important security requirements of MANETs are certain discovery, isolation of the in-appropriate nodes and some location policy regarding node location and network structure. From security aspect of MANETs, there are basically two types of attacks on the network, i.e., active attack which inserts arbitrary packets and attempts to disrupt the network operation and passive attack which do not disrupt the network operation [7,11]. Another important aspect regarding security in MANETs is that each node in the network relies upon the other nodes to forward the data packets while during communication. Hence, before communication in MANETs one must tackle efficiently with the presented issues.
Routing in Wireless Adhoc Networking
The no presence of fixed infrastructure in MANETs creates certain demanding challenges and difficulties. The biggest challenge among them is routing. Routing is the method of selecting paths in a network along which data need to be communicated to the desired destination through nodes [1,9]. An ad hoc network is a tradition, or standard, routing protocol that controls how routers choose which way to route the data packets between source(s) and destination(s) in MANETs. In MANETs, nodes don’t begin acquainted with the topology of their networks; rather, they need to find it [6,7]. The fundamental thought is that a new node may declare its presence and ought to listen for various announcements broad-casted by its neighbors. In the process each nodes learns about near-by nodes and how to reach them and may announce that it can get to that node as well. The routing procedure normally follows forwarding on the basis of routing tables which keep up a record of route(s) to different network destinations [2,5]. In this way, building routing tables, which are held in the memory of router, is critical for effective routing.
The development of laptops and 802.11/Wi-Fi wireless networking administration has made MANETs a famous look into point since the 1990s. Numerous academic papers assess protocols and capabilities expecting fluctuating degrees of mobility inside a bounded space, more often than not with all nodes inside a couple of hops from each other and typically with nodes sending information at a constant rate. Multiple protocols are then evaluated in view of the packet drop rate, expected routing load, expected end-toend- delay, and other different measures [3,11]. The proposed techniques for routing protocols could be gathered in to three classes: proactive (or table-driven), reactive (or on-request) and hybrid protocols. Indeed, even the reactive protocols have turned into the standard for MANET routing.
MANETs are suited for use in circumstances where network infrastructure is either not accessible on the other hand not trusted. For example, a communication network for military officers in a field, a mobile network of smart phones in a meeting or campus setting, temporary workplaces in a crusade home office, biological research in wireless sensor networks, mobile social networks like Facebook, My-Space and Twitter, and mobile mesh networks for Wi-Fi devices [8,10]. The main challenges in MANETs are taking advantage of wireless mesh nodes to build a robust backbone network for interconnecting all mesh nodes, and probably some external gateways to/from the Internet. Describing a class of MANET routing protocols that, by taking advantage of network backbone can sort out the best path(s) for traffic engineering by solving the Multi Commodity Flow (MCF) problem inside the network to/from the Internet and supporting dynamic user topology and mobility among wireless mesh networks [11]. These challenges are mainly centered on the major areas like, MANETs application scenarios, communication protocols, hardware and software requirements and QoS based optimization techniques.
References
- I Okundaye, T Kunz, S Gulder (2014) Inter-domain Routing for Tactical Mobile Ad-hoc Networks. IEEE 80th Vehicular Technology Conference (VTC2014-Fall) 2014: 1-6.
- S Shavali Relative weight optimized linking scheme for route optimization in ADHOC network.
- K Holter, A Hafslund, FY Li, K Af Eoevsthus (2005) Design and implementation of wireless OSPF for mobile ad hoc networks in Scandinavian Workshop on Wireless Ad-hoc Networks (ADHOC 06), Stockholm, Sweden, 2005.
- N Du, H Yang, C Wang (2012) An Optimized OSPF Routing Protocol for Mobile Ad-hoc Networks. Journal of Networks 7: 1456-1463.
- E Baccelli, JAC (2010) Fuertes, P Jacquet (2010) Ospf over multi-hop ad hoc wireless communications,” International journal of Computer Networks and Communications 2: 37-56.
- JA Cordero, E Baccelli, P Jacquet (2010) OSPF over multi-hop ad hoc wireless communications. INRIA.
- V Kolar, NB Abu-Ghazaleh (2006) A multi-commodity flow approach for globally aware routing in multi-hop wireless networks. in Fourth Annual IEEE International Conference on Pervasive Computing and Communications (PERCOM’06) 2006: 10-317.
- J Loo, JL Mauri, JH Ortiz (2016) Mobile ad hoc networks: current status and future trends: CRC Press.
- M Conti, S Giordano (2014) Mobile ad hoc networking: milestones, challenges, and new research directions. IEEE Communications Magazine 52: 85-96.
- G Breed (2007) Wireless ad hoc networks: basic concepts. High frequency electronics 1: 44-47.
- H Zeng, M Li, H. Liu, X Jia (2008) Efficient flooding in mobile ad hoc networks. Nova Science Publishers.

Top Editors
-

Mark E Smith
Bio chemistry
University of Texas Medical Branch, USA -

Lawrence A Presley
Department of Criminal Justice
Liberty University, USA -

Thomas W Miller
Department of Psychiatry
University of Kentucky, USA -

Gjumrakch Aliev
Department of Medicine
Gally International Biomedical Research & Consulting LLC, USA -

Christopher Bryant
Department of Urbanisation and Agricultural
Montreal university, USA -

Robert William Frare
Oral & Maxillofacial Pathology
New York University, USA -

Rudolph Modesto Navari
Gastroenterology and Hepatology
University of Alabama, UK -

Andrew Hague
Department of Medicine
Universities of Bradford, UK -

George Gregory Buttigieg
Maltese College of Obstetrics and Gynaecology, Europe -

Chen-Hsiung Yeh
Oncology
Circulogene Theranostics, England -
.png)
Emilio Bucio-Carrillo
Radiation Chemistry
National University of Mexico, USA -
.jpg)
Casey J Grenier
Analytical Chemistry
Wentworth Institute of Technology, USA -
Hany Atalah
Minimally Invasive Surgery
Mercer University school of Medicine, USA -

Abu-Hussein Muhamad
Pediatric Dentistry
University of Athens , Greece
The annual scholar awards from Lupine Publishers honor a selected number Read More...